diff --git a/authentication.md b/authentication.md
index 7cf49a2..5147d9b 100644
--- a/authentication.md
+++ b/authentication.md
@@ -15,6 +15,8 @@
- [Setting up Keycloak](#2-setup-keycloak-users)
- [Configuring Dashy for Keycloak](#3-enable-keycloak-in-dashy-config-file)
- [Toubleshooting Keycloak](#troubleshooting-keycloak)
+- [OIDC Auth](#oidc)
+ - [authentik](#authentik)
- [Alternative Authentication Methods](#alternative-authentication-methods)
- [VPN](#vpn)
- [IP-Based Access](#ip-based-access)
@@ -283,6 +285,7 @@ appConfig:
oidc:
clientId: [registered client id]
endpoint: [OIDC endpoint]
+ scope: [The scope(s) to request from the OIDC provider]
```
Because Dashy is a SPA, a [public client](https://datatracker.ietf.org/doc/html/rfc6749#section-2.1) registration with PKCE is needed.
@@ -311,10 +314,187 @@ identity_providers:
- 'groups'
```
-Groups and roles will be populated and available for controlling display similar to [Keycloak](#Keycloak) abvoe.
+Groups and roles will be populated and available for controlling display similar to [Keycloak](#Keycloak) above.
---
+### authentik
+
+This documentation is specific to `authentik`, however it may be useful in getting other idP's working with `Dashy`.
+
+This guide will only walk through the following:
+ * Creating and configuring an OIDC provider
+ * Creating and configuring an application
+ * Assigning groups
+ * Configuring `Dashy` to use the OIDC client
+ * Show quick examples of how to hide/show `pages`, `items`, and `sections` using OIDC groups
+
+This guide assumes the following:
+ * You have a working instance of `authentik` terminated with SSL
+ * You have a working instance of `Dashy` terminated with SSL
+ * Users and groups are provisioned
+ * You are familiar with how `authentik` works in case you need to do further troubleshooting that is outside the scope of this guide.
+
+>[!TIP]
+>It it recommended that you create groups specific for `Dashy`. Groups will allow you to display content based on group membership as well as limiting user access to `Dashy`. If you do not need this functionality, then you can forgo creating specific groups.
+
+>[!TIP]
+>You can use the application wizard to create the provider and application at one time. This is the recommended route, but only the manual process will be outlined in this guide.
+
+
+
+#### 1. Create an OIDC provider
+
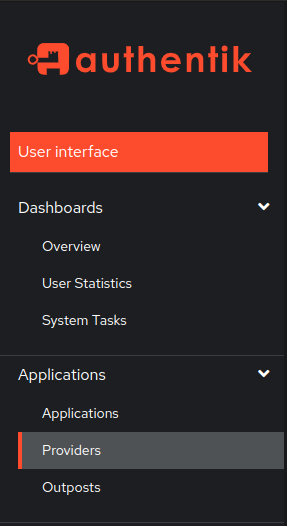
+Login to the admin console for `authentik`. Go to `Applications` > `Providers`. Click `Create`.
+
+
+
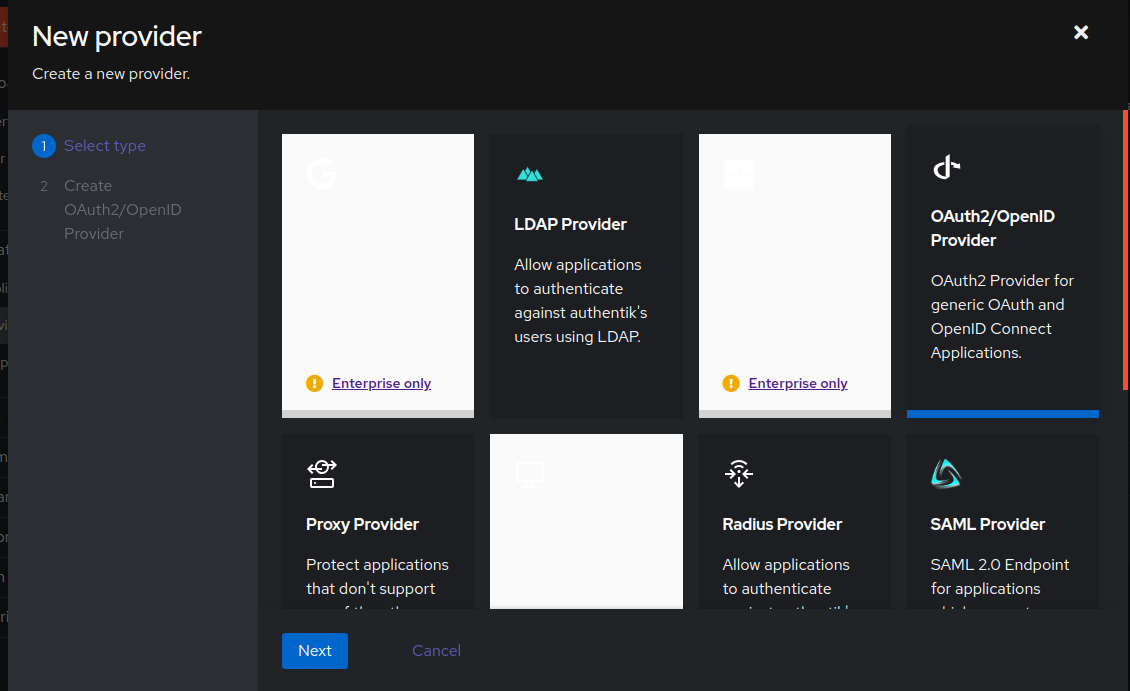
+A dialog box will pop-up, select the `OAuth2/OpenID Provider`. Click `Next`.
+
+
+
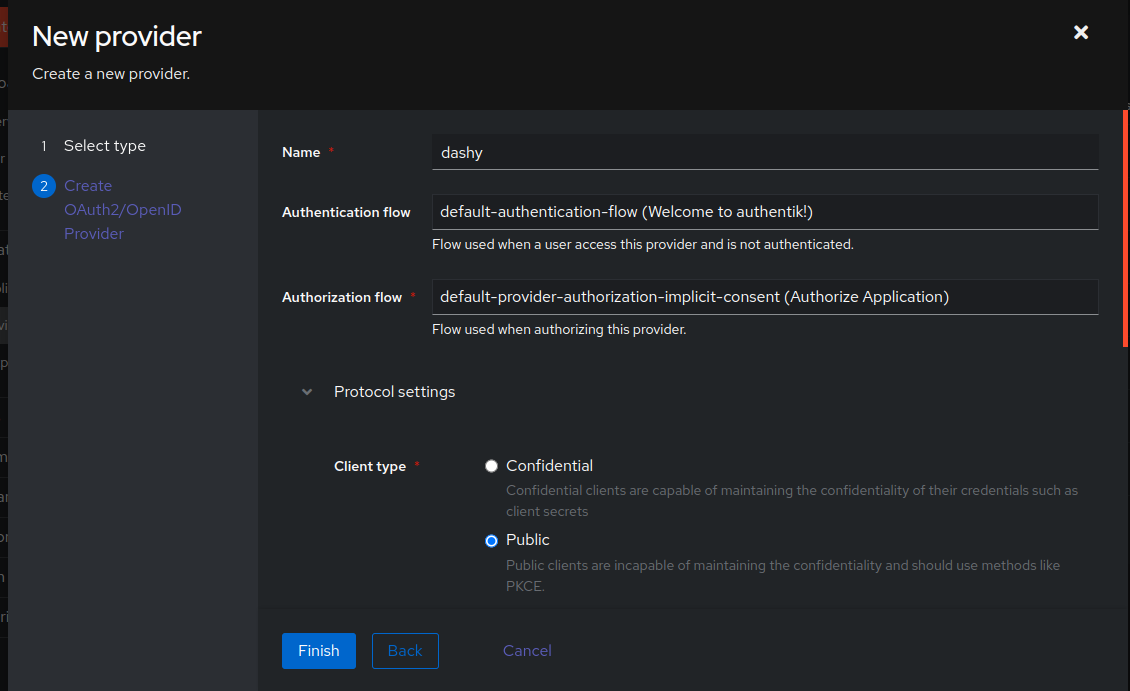
+On the next page of the wizard, set the `Name`, `Authentication flow`, and `Authorization flow`. See example below. Using the `default-provider-authorization-implicit-consent` authorization flow on internal services and `default-provider-authorization-explicit-consent` on external services is a common practice. However, it is fully up to you on how you would like to configure this option. `Implicit` will login directly without user consent, `explicit` will ask if the user approves the service being logged into with their user credentials.
+
+
+
+Scroll down and configure the `Protocol settings`. Set the `Client type` to `Public`. Add the `Redirect URIs/Origins (RegEx)`. If the site is hosted at `dashy.lan.domain.com`, then you would enter as the example below.
+
+>[!NOTE]
+>If you have an internal and external domain for `Dashy`, enter both URI's. Enter each URI on a new line.
+
+
+
+Scroll down to set the `Signing Key`. It is recommended to use the built in `authentik Self-signed Certificate` here unless you have special needs for your own custom cert.
+
+
+
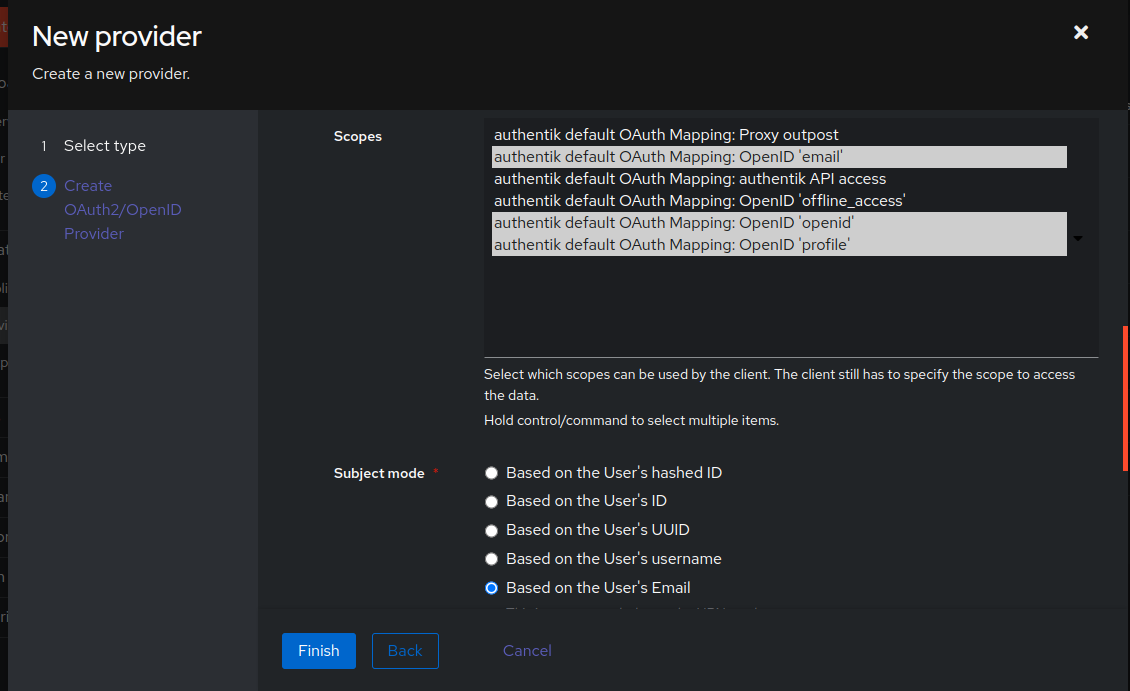
+Expand `Advanced protocol settings` then verify the `Scopes` are set to what is highlighted in `white` below. Set the `Subject mode` to `Based on the Users's Email`.
+
+
+
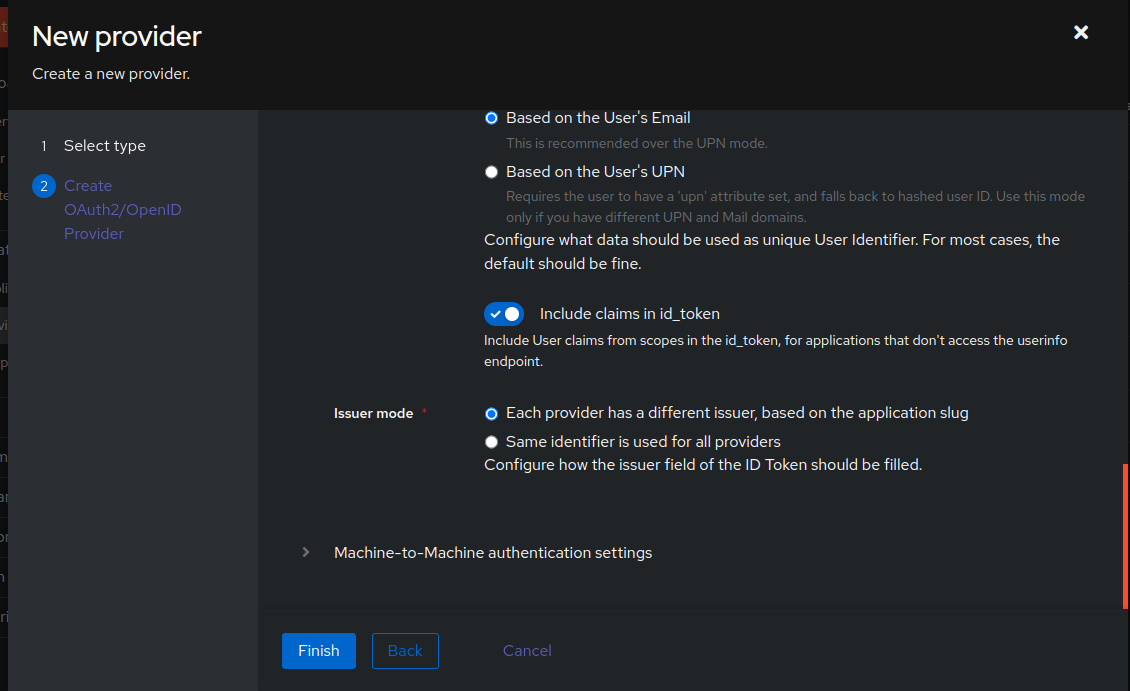
+Lastly, toggle `Include claims in id_token` to on. Click `Finish` to complete creating the provider.
+
+
+
+Grab the generated `Client ID` and `OpenID Configuration Issuer` URL by clicking the newly created provider as this will use this later when `Dashy` is configured to use the OIDC auth mechanism. In this tutorial, what was generated is used below. Obviously adjust the `Client ID` that was generated and use your domain here for the `issuer`.
+```
+Client ID: pzN9DCMLqHTTatgtYFg50cl0jn1NmCyBC3wreX15
+OpenID Configuration Issuer: https://auth.domain.com/application/o/dashy/
+```
+
+#### 2. Create an application
+
+Make sure you are still in the `authentik` admin console then go to `Applications` > `Applications`. Click `Create`.
+
+
+
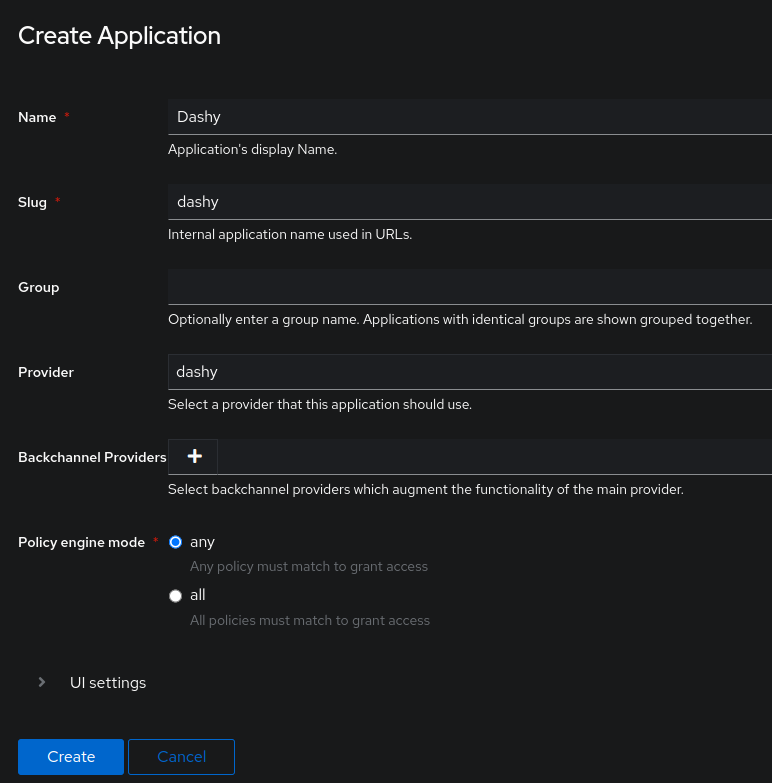
+Next, it is required to give a user facing `Name`, `Slug` and assign the newly created provider. Use the example below if you have been following the guide. If you have used your own naming, then adjust accordingly. Click `Create` once you are done.
+
+
+
+>[!TIP]
+>Open the application in a new tab from the `authentik` user portal and upload a custom icon. You can also enter a user facing `Description` that the user would see.
+
+
+
+#### 3. *(Optional)* Limiting access via `authentik` with groups
+
+If you would like to deny `Dashy` access from specific users who are not within `authentik` based groups, you bind them to the application you just created now. `authentik` will deny access to those who are not members of this group or groups. If you want to allow everyone access from your `authentik` instance, skip this step.
+
+Make sure you are still in the `authentik` admin console then go to `Applications` > `Applications`. Click the newly created `Dashy` application.
+
+
+
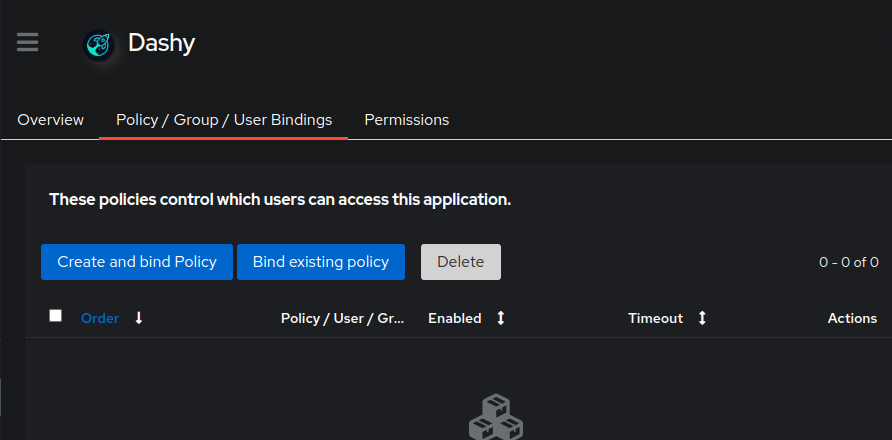
+Click the `Policy/Group/User Bindings` tab at the top, then click `Bind existing policy`. This assumes you have already created the groups you want to use for `Dashy` and populated users in those groups.
+
+
+
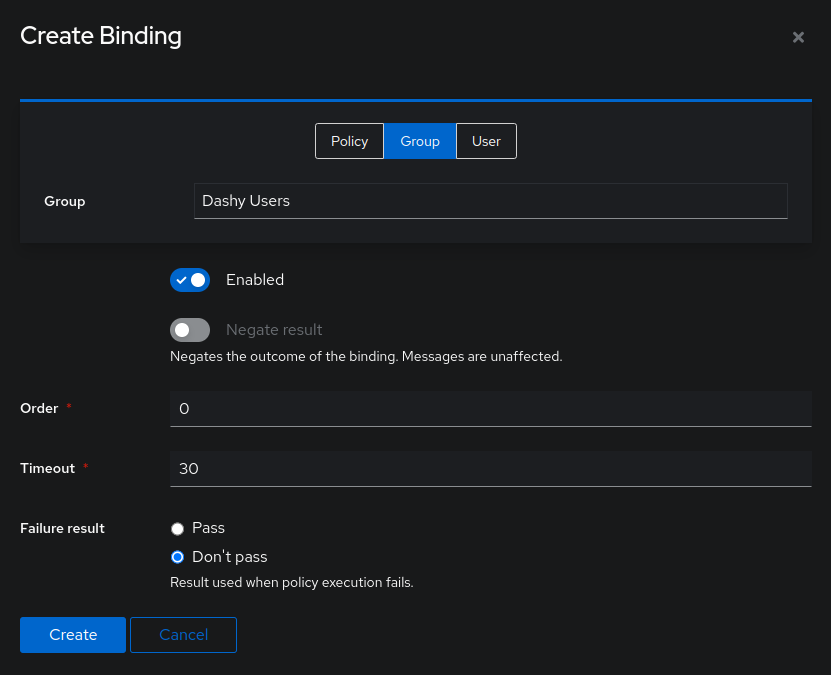
+Click `Group` for the binding type. Under `Group` select the appropriate group you would like to bind. Make sure `Enabled` is toggeled on. Click `Create`.
+
+
+
+`Dashy` will now be scoped only to users within the assigned groups you have bound the application to. Keep adding groups if you would like to adjust the dashboard visibilty based on group membership.
+
+#### 4. Configure `Dashy` to use OIDC client
+
+>[!IMPORTANT]
+>It is highly recommended to edit your `conf.yml` directly for this step.
+
+>[!CAUTION]
+>Do not make the same mistake many have made here by including the fully qualified address for the `OpenID Configuration URL`. `Dashy` will append the `.well-known` configuration automatically. If the `.well-known` URI is included the app will get redirect loops and `400` errors.
+
+Enter the `Client ID` in the `clientId` field and `OpenID Configuration Issuer` in the `endpoint` field.
+
+Below is how to configure the `auth` section in the yaml syntax. Once this is enabled, when an attempt to access `Dashy` is made it will now redirect you to the `authentik` login page moving forward.
+
+```
+appConfig:
+ theme: glass
+ layout: auto
+ iconSize: medium
+ auth:
+ enableOidc: true
+ oidc:
+ clientId: pzN9DCMLqHTTatgtYFg50cl0jn1NmCyBC3wreX15
+ endpoint: https://auth.domain.com/application/o/dashy/
+```
+
+#### 5. *(OPTIONAL)* Example snippets for dashboard visibility
+
+Using the `hideForKeycloakUsers` configuration option is needed to use the `authentik` groups that were created previously.
+
+Adjusting `pages` visibility:
+```
+pages:
+ - name: App Management
+ path: appmgmt.yml
+ displayData:
+ hideForKeycloakUsers:
+ groups:
+ - Dashy Users
+ - name: Network Management
+ path: network.yml
+ displayData:
+ hideForKeycloakUsers:
+ groups:
+ - Dashy Users
+```
+
+Adjusting `items` visibility:
+```
+ items:
+ - title: Authentik Admin
+ icon: authentik.svg
+ url: https://auth.domain.com/if/admin/
+ target: newtab
+ id: 0_1472_authentikadmin
+ displayData:
+ hideForKeycloakUsers:
+ groups:
+ - Dashy Users
+ - title: Authentik User
+ icon: authentik-light.png
+ url: https://auth.domain.com/if/user/
+ target: newtab
+ id: 1_1472_authentikuser
+```
+
+Adjusting `sections` visibility:
+```
+sections:
+ - name: Authentication
+ displayData:
+ sortBy: default
+ rows: 2
+ cols: 1
+ collapsed: false
+ hideForGuests: false
+ hideForKeycloakUsers:
+ groups:
+ - Dashy Users
+```
+---
+
## Alternative Authentication Methods
If you are self-hosting Dashy, and require secure authentication to prevent unauthorized access, then you can either use Keycloak, or one of the following options:
diff --git a/configuring.md b/configuring.md
index acf9357..c10088f 100644
--- a/configuring.md
+++ b/configuring.md
@@ -202,6 +202,7 @@ For more info, see the **[Authentication Docs](/docs/authentication.md)**
--- | --- | --- | ---
**`clientId`** | `string` | Required | The client id registered in the OIDC server
**`endpoint`** | `string` | Required | The URL of the OIDC server that should be used.
+**`scope`** | `string` | Required | The scope(s) to request from the OIDC provider
**[⬆️ Back to Top](#configuring)**
diff --git a/credits.md b/credits.md
index 70f615b..caf40d4 100644
--- a/credits.md
+++ b/credits.md
@@ -120,7 +120,7 @@
-  +
+ 
GT
@@ -154,6 +154,13 @@
Terminal Trove
|
+
+
+  +
+
+ Null
+
+ |
 @@ -347,6 +354,20 @@
@@ -347,6 +354,20 @@
|
+
+
+  +
+
+ Null
+
+ |
+
+
+  +
+
+ Aaron Echols
+
+ |
 @@ -374,7 +395,8 @@
@@ -374,7 +395,8 @@
Remygrandin
- |
+
+
 @@ -388,8 +410,7 @@
@@ -388,8 +410,7 @@
Totto16
- |
-
+
 @@ -417,7 +438,8 @@
@@ -417,7 +438,8 @@
Bogyeong Kim
- |
+
+
 @@ -431,8 +453,7 @@
@@ -431,8 +453,7 @@
Stanly0726
- |
-
+
 @@ -460,7 +481,8 @@
@@ -460,7 +481,8 @@
Joey Miller
- |
+
+
 @@ -474,8 +496,7 @@
@@ -474,8 +496,7 @@
Null
- |
-
+
 @@ -503,7 +524,8 @@
@@ -503,7 +524,8 @@
Null
- |
+
+
 @@ -517,8 +539,7 @@
@@ -517,8 +539,7 @@
Null
- |
-
+
 @@ -546,7 +567,8 @@
@@ -546,7 +567,8 @@
Null
- |
+
+
 @@ -560,8 +582,7 @@
@@ -560,8 +582,7 @@
CHAIYEON CHO
- |
-
+
 @@ -589,20 +610,6 @@
@@ -589,20 +610,6 @@
Al-Ayham Saleh
- |
-
-
-  -
-
- Null
-
- |
-
-
-  -
-
- Ryan Turner
-
|
|
@@ -662,6 +669,35 @@
Steven Kast
|
+
+
+  +
+
+ Thibaut
+
+ |
+
+
+  +
+
+ Ángel Fernández Sánchez
+
+ |
+
+
+  +
+
+ Ryan Turner
+
+ |
+
+
+  +
+
+ Null
+
+ |
+
 @@ -689,8 +725,7 @@
@@ -689,8 +725,7 @@
Nicholas Malcolm
- |
-
+
 @@ -704,7 +739,8 @@
@@ -704,7 +739,8 @@
Michael D
- |
+
+
 @@ -719,21 +755,6 @@
Mert Sefa AKGUN
@@ -719,21 +755,6 @@
Mert Sefa AKGUN
|
-
-
-  -
-
- Maxime Moreillon
-
- |
-
-
-  -
-
- Ángel Fernández Sánchez
-
- |
-
 @@ -761,6 +782,14 @@
@@ -761,6 +782,14 @@
Null
+ |
+
+
+
+  +
+
+ Noé Busson
+
|
@@ -775,8 +804,7 @@
Laker Turner
- |
-
+
 @@ -797,7 +825,8 @@
@@ -797,7 +825,8 @@
Jnach
- |
+
+
 @@ -818,8 +847,7 @@
@@ -818,8 +847,7 @@
Null
- |
-
+
 @@ -840,7 +868,8 @@
@@ -840,7 +868,8 @@
Null
- |
+
+
 @@ -856,18 +885,17 @@
@@ -856,18 +885,17 @@
|
-
-  +
+
+
+ 
- Thibaut
+ Will Browning
- |
-
+
-
-  +
+
+
+ 
- Max Kulik
+ Null
|
@@ -883,7 +911,8 @@
Dylan Bersans
- |
+
+
 @@ -904,8 +933,7 @@
@@ -904,8 +933,7 @@
Doug Lock
- |
-
+
 @@ -926,7 +954,8 @@
@@ -926,7 +954,8 @@
Null
- |
+
+
 @@ -947,8 +976,7 @@
@@ -947,8 +976,7 @@
Celestial.y
- |
-
+
 @@ -969,7 +997,8 @@
@@ -969,7 +997,8 @@
Begin
- |
+
+
 @@ -990,8 +1019,7 @@
@@ -990,8 +1019,7 @@
Aly Mohamed
- |
-
+
 @@ -1006,6 +1034,21 @@
0n1cOn3
@@ -1006,6 +1034,21 @@
0n1cOn3
|
+
+
+  +
+
+ Maxime Moreillon
+
+ |
+
+
+
+  +
+
+ Max Kulik
+
+ |
 @@ -1033,15 +1076,15 @@
@@ -1033,15 +1076,15 @@
Leonardo Colman Lopes
- |
-
+

Kieren Connell
- |
+
+
 @@ -1076,15 +1119,15 @@
@@ -1076,15 +1119,15 @@
Ishan Jain
- |
-
+

Iaroslav Dronskii
- |
+
+
 @@ -1119,28 +1162,21 @@
@@ -1119,28 +1162,21 @@
Garrett Brown
- |
-
+

FormatToday
- |
+
+

Fedello
- |
-
-
-  -
-
- Null
-
|
diff --git a/privacy.md b/privacy.md
index 1c150e5..b915c17 100644
--- a/privacy.md
+++ b/privacy.md
@@ -132,8 +132,8 @@ Dashy supports [Widgets](/docs/widgets.md) for displaying dynamic content. Below
- [BlockCypher Privacy Policy](https://www.blockcypher.com/privacy.html)
- **[Code::Stats](/docs/widgets.md#code-stats)**: `https://codestats.net`
- [Code::Stats Privacy Policy](https://codestats.net/tos#privacy)
-- **[AnonAddy](/docs/widgets.md#anonaddy)**: `https://app.anonaddy.com`
- - [AnonAddy Privacy Policy](https://anonaddy.com/privacy/)
+- **[addy.io](/docs/widgets.md#addyio)**: `https://app.addy.io`
+ - [addy.io Privacy Policy](https://addy.io/privacy/)
- **[Vulnerability Feed](/docs/widgets.md#vulnerability-feed)**: `https://www.cvedetails.com`
- [CVE Details Privacy Policy](https://www.cvedetails.com/privacy.php)
- **[Exchange Rate](/docs/widgets.md#exchange-rates)**: `https://v6.exchangerate-api.com`
diff --git a/widgets.md b/widgets.md
index c66fa52..ac03ad5 100644
--- a/widgets.md
+++ b/widgets.md
@@ -18,7 +18,7 @@ Dashy has support for displaying dynamic content in the form of widgets. There a
- [Crypto Wallet Balance](#wallet-balance)
- [Code Stats](#code-stats)
- [Mullvad Status](#mullvad-status)
- - [Email Aliases (AnonAddy)](#anonaddy)
+ - [Email Aliases (addy.io)](#addyio)
- [Vulnerability Feed](#vulnerability-feed)
- [Exchange Rates](#exchange-rates)
- [Public Holidays](#public-holidays)
@@ -67,6 +67,7 @@ Dashy has support for displaying dynamic content in the form of widgets. There a
- [Drone CI Build](#drone-ci-builds)
- [Linkding](#linkding)
- [Uptime Kuma](#uptime-kuma)
+ - [Tactical RMM](#tactical-rmm)
- **[System Resource Monitoring](#system-resource-monitoring)**
- [CPU Usage Current](#current-cpu-usage)
- [CPU Usage Per Core](#cpu-usage-per-core)
@@ -573,11 +574,11 @@ _No Options._
---
-### AnonAddy
+### addy.io
-[AnonAddy](https://anonaddy.com/) is a free and open source mail forwarding service. Use it to protect your real email address, by using a different alias for each of your online accounts, and have all emails land in your normal inbox(es). Supports custom domains, email replies, PGP-encryption, multiple recipients and more
+[addy.io](https://addy.io/) is a free and open source mail forwarding service. Use it to protect your real email address, by using a different alias for each of your online accounts, and have all emails land in your normal inbox(es). Supports custom domains, email replies, PGP-encryption, multiple recipients and more
-This widget display email addresses / aliases from AnonAddy. Click an email address to copy to clipboard, or use the toggle switch to enable/ disable it. Shows usage stats (bandwidth, used aliases etc), as well as total messages received, blocked and sent. Works with both self-hosted and managed instances of AnonAddy.
+This widget display email addresses / aliases from addy.io. Click an email address to copy to clipboard, or use the toggle switch to enable/ disable it. Shows usage stats (bandwidth, used aliases etc), as well as total messages received, blocked and sent. Works with both self-hosted and managed instances of addy.io.

@@ -585,8 +586,8 @@ This widget display email addresses / aliases from AnonAddy. Click an email addr
**Field** | **Type** | **Required** | **Description**
--- | --- | --- | ---
-**`apiKey`** | `string` | Required | Your AnonAddy API Key / Personal Access Token. You can generate this under [Account Settings](https://app.anonaddy.com/settings)
-**`hostname`** | `string` | _Optional_ | If your self-hosting AnonAddy, then supply the host name. By default it will use the public hosted instance
+**`apiKey`** | `string` | Required | Your addy.io API Key / Personal Access Token. You can generate this under [Account Settings](https://app.addy.io/settings)
+**`hostname`** | `string` | _Optional_ | If your self-hosting addy.io, then supply the host name. By default it will use the public hosted instance
**`apiVersion`** | `string` | _Optional_ | If you're using an API version that is not version `v1`, then specify it here
**`limit`** | `number` | _Optional_ | Limit the number of emails shown per page. Defaults to `10`
**`sortBy`** | `string` | _Optional_ | Specify the sort order for email addresses. Defaults to `updated_at`. Can be either: `local_part`, `domain`, `email`, `emails_forwarded`, `emails_blocked`, `emails_replied`, `emails_sent`, `created_at`, `updated_at` or `deleted_at`. Precede with a `-` character to reverse order.
@@ -614,7 +615,7 @@ This widget display email addresses / aliases from AnonAddy. Click an email addr
- **Auth**: 🔴 Required
- **Price**: 🟠 Free for Self-Hosted / Free Plan available on managed instance or $1/month for premium
- **Host**: Self-Hosted or Managed
-- **Privacy**: _See [AnonAddy Privacy Policy](https://anonaddy.com/privacy/)_
+- **Privacy**: _See [addy.io Privacy Policy](https://addy.io/privacy/)_
---
@@ -2333,6 +2334,41 @@ Linkding is a self-hosted bookmarking service, which has a clean interface and i
- **Host**: Self-Hosted (see [Uptime Kuma](https://github.com/louislam/uptime-kuma) )
- **Privacy**: _See [Uptime Kuma](https://github.com/louislam/uptime-kuma)_
+---
+
+### Tactical RMM
+
+[Tactical RMM](https://github.com/amidaware/tacticalrmm) is a self-hosted remote monitoring & management tool.
+
+
+
+
+#### Options
+
+| **Field** | **Type** | **Required** | **Description** |
+| ------------ | -------- | ------------ | ------------------------------------------------------------------------ |
+| **`url`** | `string` | Required | The status endpoint URL (https://api.example.com/core/status/) |
+| **`token`** | `string` | Required | The MON_TOKEN (see https://docs.tacticalrmm.com/tipsntricks/#monitor-your-trmm-instance-via-the-built-in-monitoring-endpoint). |
+
+#### Example
+
+```yaml
+- type: trmm
+ useProxy: true
+ options:
+ token: PkPVKMzbmXgeQDlJWb0WXYvsIk3JvZyadURud2cSTdMia6hUbQ
+ url: https://api.example.com/core/status/
+```
+
+#### Info
+
+- **CORS**: 🟠 Proxied
+- **Auth**: 🟢 Required
+- **Price**: 🟢 Free
+- **Host**: Self-Hosted (see [Tactical RMM](https://github.com/amidaware/tacticalrmm) )
+- **Privacy**: _See [Tactical RMM](https://github.com/amidaware/tacticalrmm)_
+
+
---
## System Resource Monitoring
